Azure has four main approaches to configure explicit outbound connectivity for your VMs, each with different levels of complexity, cost, and security capabilities.
Option 1: Public IP assignment
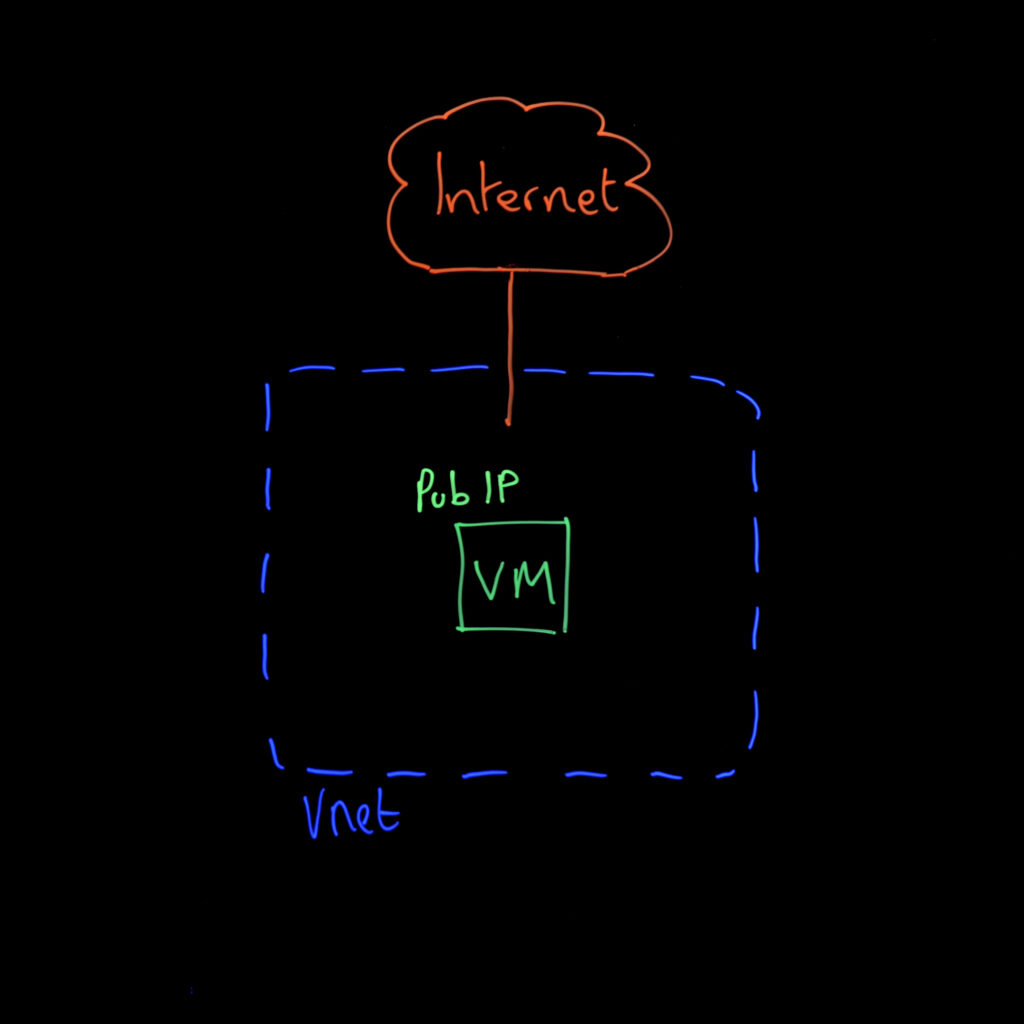
The most straightforward approach is to assign a public IP directly to your virtual machine. You can do this during VM creation or afterwards by modifying the network interface configuration.
- When to use it: Small deployments where individual VM internet access is acceptable and network complexity is minimal.
- Pros: Simple to implement, consistent public IP address, can be configured during or after VM deployment.
- Cons: Each VM has direct internet exposure, limited security controls, not cost-effective at scale, challenging to manage across multiple VMs.
- Key consideration: Whilst this solves the changing IP problem, it doesn’t address the fundamental security concerns of having VMs directly exposed to the internet.
Option 2: Standard Load Balancer with outbound rules
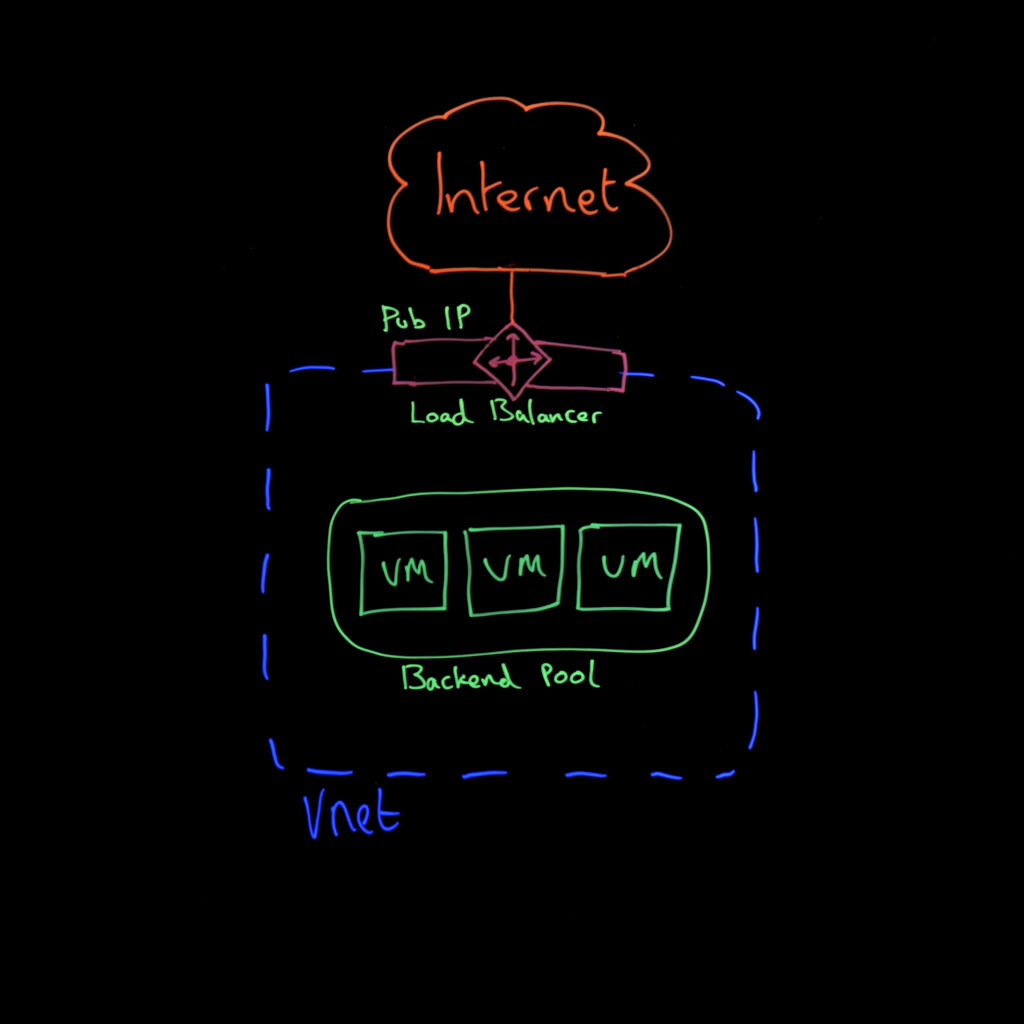
This approach uses a Standard Load Balancer with outbound rules to provide source NAT for your VMs. Your virtual machines sit in a backend pool behind the load balancer, which presents a single public IP for all outbound traffic.
- When to use it: When you already have a Standard Load Balancer in place and don’t have excessive traffic requirements.
- Pros: Cost-effective if you’re already using load balancing, flexible control over outbound connections, can assign multiple public IPs for different VM groups.
- Cons: Still relies on Network Security Groups for destination control. It adds complexity if you don’t need load balancing. Outbound rules won’t apply if VMs have instance-level public IPs.
- Key considerations: As soon as you place a VM in a load balancer’s backend pool, default outbound access is automatically disabled. Internal load balancers don’t provide outbound connectivity.
Option 3: NAT Gateway (Microsoft’s recommended)
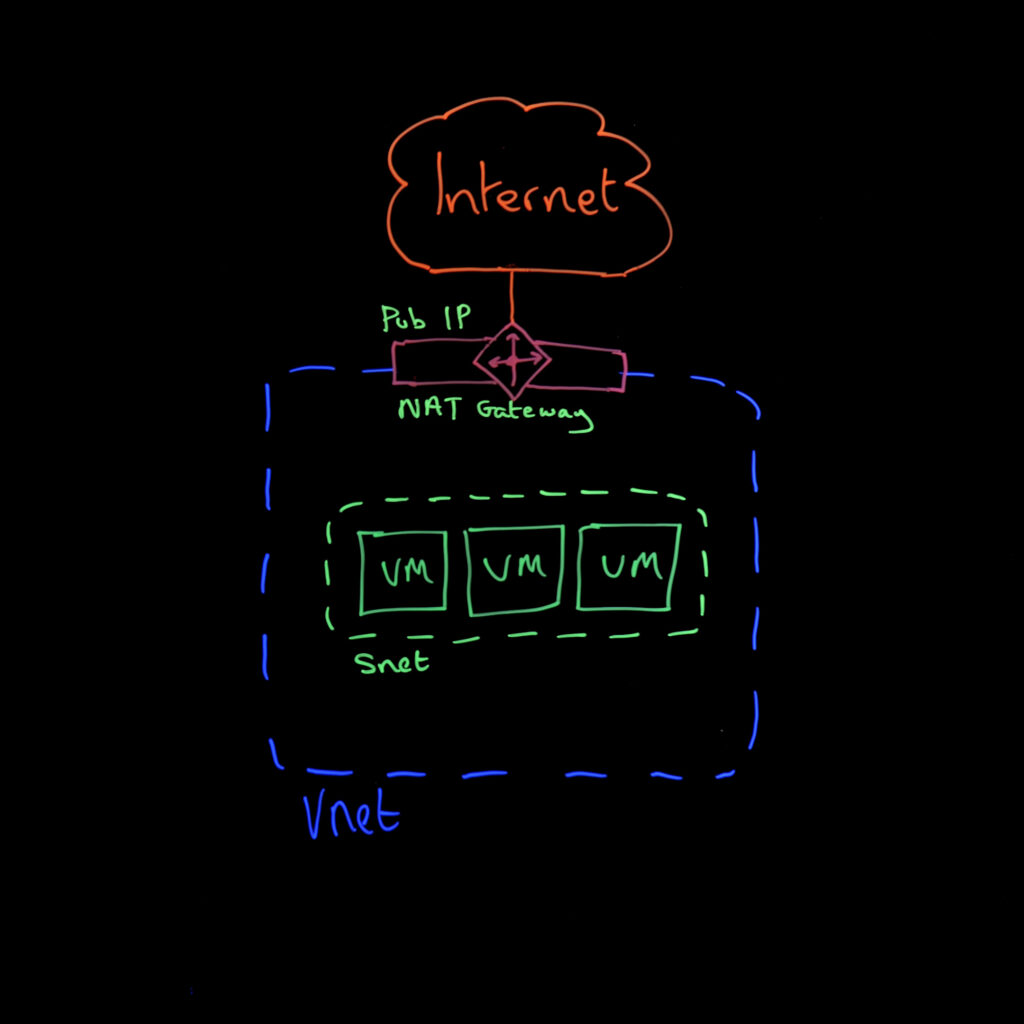
NAT Gateway is a fully managed, highly resilient network address translation service that allows all instances in a private subnet to connect outbound to the internet.
- When to use it: For most scenarios where you need reliable, scalable outbound connectivity without the complexity of a full security appliance.
- Pros: Simple to deploy and configure, excellent performance and scalability, cost-effective compared to firewall solutions, automatically overrides default routes, and can serve multiple subnets from a hub VNet.
- Cons: Limited to basic NAT functionality, not supported in secured Virtual WAN environments, and fewer security controls than firewall-based solutions.
- Key considerations: Microsoft explicitly recommends NAT Gateway as the preferred method for outbound internet access, mostly due to its simplicity and cost-effectiveness. Once deployed, it takes precedence over user-defined routes, making configuration straightforward.
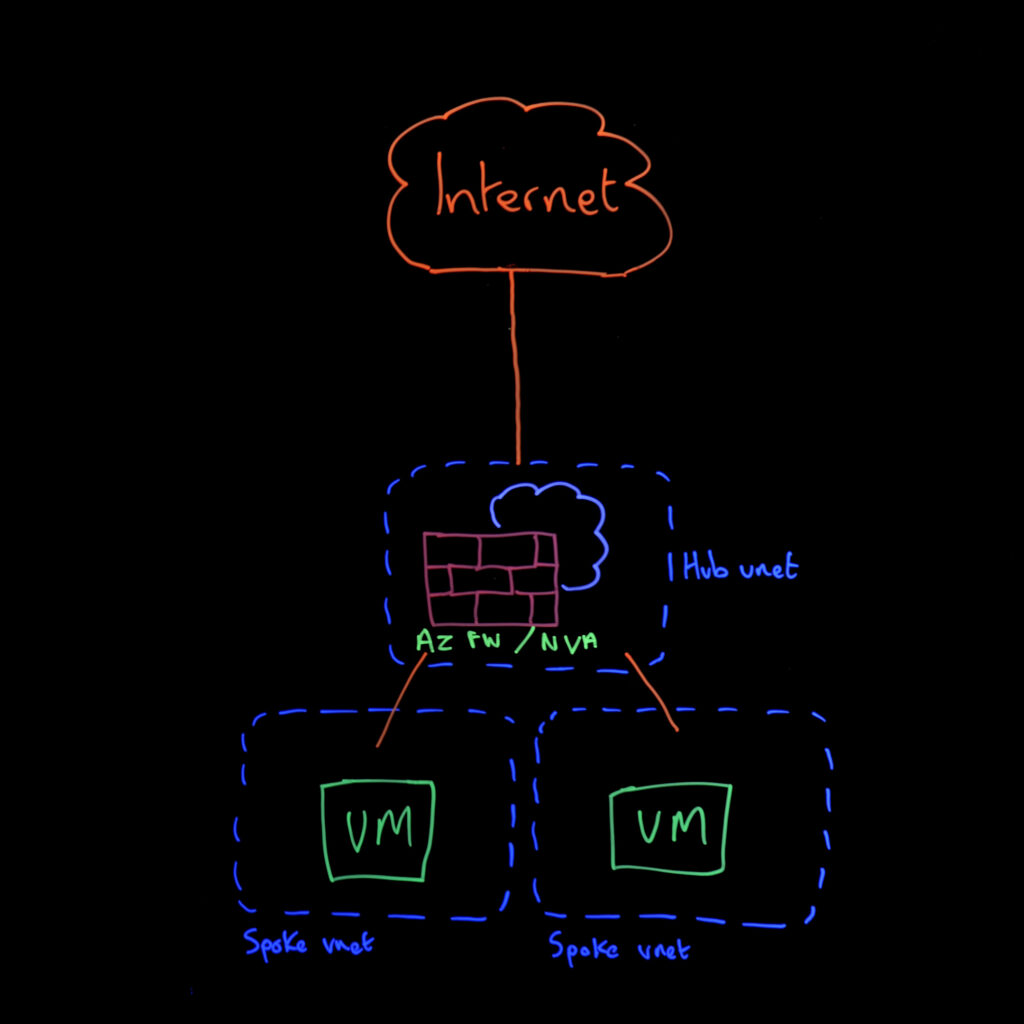
Option 4: Azure Firewall or Network Virtual Appliances