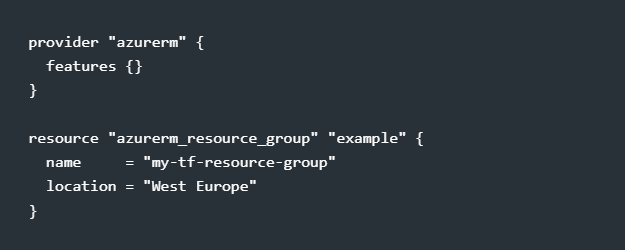
Terraform is powerful, but mistakes can cause outages, misconfigurations, and security risks. Avoid these common pitfalls:
Hardcoding Secrets
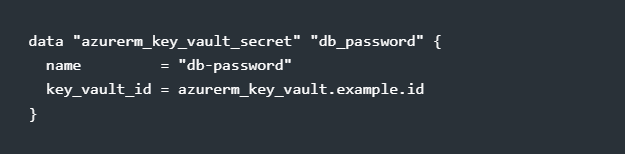
Why it’s a problem: Credentials and API keys stored in plain text can be leaked, compromised, or accidentally committed to Git.
✅ Solution: Always store secrets in a secrets manager like Azure Key Vault or Terraform Cloud Vault. Use sensitive = true in variables to prevent exposure in logs.
Skipping terraform plan
Why it’s a problem: Applying Terraform changes blindly can delete or modify resources unintentionally, leading to downtime.
✅ Solution: Always run terraform plan
This allows teams to review exactly what Terraform will change before applying.
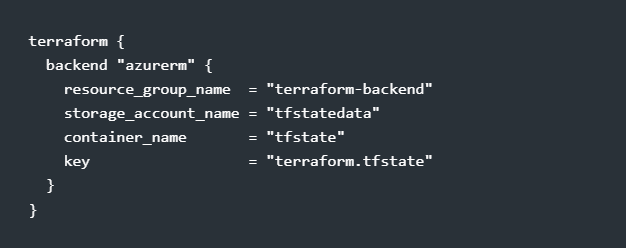
Poor State Management
Why it’s a problem: Terraform state tracks infrastructure, and losing or corrupting it can result in orphaned resources, conflicting deployments, or infrastructure drift.
✅ Solution: Use remote state storage with state locking to avoid conflicts when multiple engineers are working on the same infrastructure.
Manual Infrastructure Changes
Why it’s a problem: Making changes directly in the Azure portal or CLI creates drift between the actual environment and Terraform’s state, leading to inconsistencies.
✅ Solution: Always use Terraform as the single source of truth. If manual changes are made, import them into Terraform state.
Not Handling Dependencies Properly
Why it’s a problem: Resources often depend on each other. If dependencies aren’t managed correctly, deployments may fail due to timing issues.
✅ Solution: Use depends_on in Terraform to specify dependencies.
Terraform is a powerful tool, but getting the fundamentals right is critical. Avoiding these common mistakes ensures secure, scalable, and reliable deployments, keeping infrastructure under control and easy to manage.